
ESET Endpoint Encryption Pro For Business
ESET Endpoint Encryption Pro is a powerful encryption managed natively by ESET remote management console. It increases your organization's data security that meets compliance regulations.
Get the level of protection that's right for your business
Robust encryption solution for emails, system disks, partitions or entire devices to achieve legal compliance.

ESET ENDPOINT ENCRYPTION PRO
A simple to use standalone encryption solution providing full remote control of endpoint encryption keys and security policy for files on hard drives, portable devices and emails.
Ensures:
✅ Zero data breaches
✅ Meet compliance requirements
✅ Seamless encryption
DATA BREACHES PREVENTION
Minimize risks of business continuity disruptions and ensure the organization and its data are protected anywhere and anytime.
FAST SEAMLESS DEPLOYMENT
Whether encryption or authentication, both solutions are tailored to keep setup time to the absolute minimum.
REGULATORY COMPLIANCE
Meet legal requirements and regulations such as GDPR, CCPA, LGPD, or POPI.
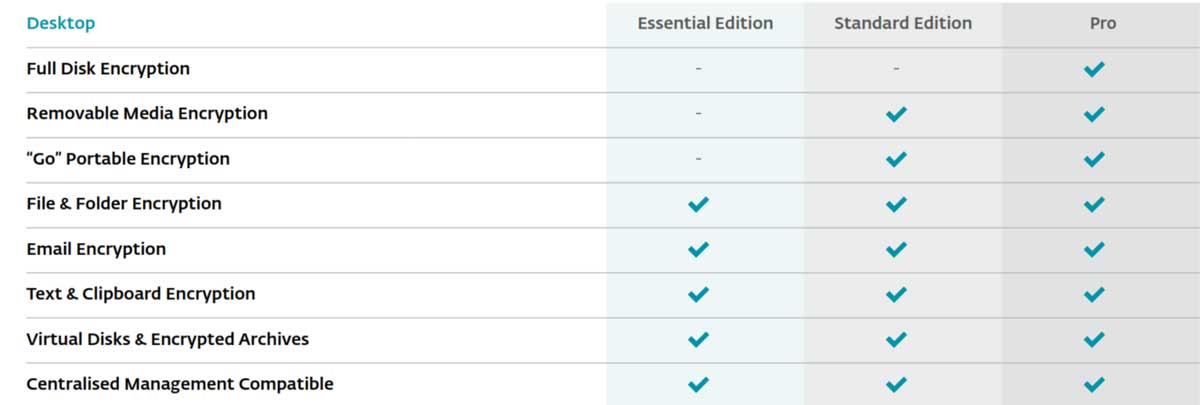
ENDPOINT ENCRYPTION PRO FEATURES
Full Disk Encryption
- Encrypt only disks and partitions you want
- On-screen keyboard which allows encrypting of Windows tablets and convertible devices
- Transparent pre-boot security using FIPS 140-2 validated, 256 bit AES Encryption
- Encryption may be started and managed remotely
- Remote user-password recovery
- Enhanced workstation screening prior encryption, including Safe Start mode
- Fully compatible with Microsoft Windows 10, 8 and 8.1, with support for UEFI and GPT
- Support of Trusted Platform Module (TPM)
Removable Media Encryption
- No extra space is reserved for encrypted content and the whole device capacity can be used by user
- Works with any USB drive, CD & DVD media
“Go” Portable Encryption
- Policy driven encryption includes “Go” portable encryption, on-device software for use on unlicensed systems
File & Folder Encryption
- Encrypt only files and folders you want
- All files moved to encrypted folder are encrypted immediately
Email Encryption
- Transparent email encryption for Outlook through a dedicated plugin
- The email can be decrypted only by recipients who share the same key as sender
- Text and clipboard encryption works with any e-mail client, including webmail
Text & Clipboard Encryption
- Encrypt all or part of a text window—web-browsers, database memo-fields or web-mail.
Virtual Disks & Encrypted Archives
- Create a secure, encrypted volume on your PC or in another location or an encrypted copy of an entire directory tree and its files.
Centralised Management Compatible
Manage any user or workstation with a standard internet connection
All commands, updates, status requests and responses posted via the Enterprise Proxy
No dependency on Active Directory or any existing server architecture installation
Secure connectivity allows control of endpoint encryption keys, security policy and software features
beyond the corporate security boundaryFull remote management, creation and removal of user accounts
Encryption Key Management
Patented technology
Add or remove any or all encryption keys
Change the encryption policy remotely and silently, without user interaction
Enterprise Server Proxy
By using the Enterprise Proxy as an intermediary, all connections from client and server are outgoing.
All information is encrypted with either RSA or AES and the connection itself is SSL encrypted
No need for own SSL certificate and additional hardware, network or firewall changes
OTHER ESET ENCRYPTION SOLUTIONS
- €10.35 – €418.88 Inc.VAT Select options This product has multiple variants. The options may be chosen on the product page
- €33.80 – €1378.02 Inc.VAT Select options This product has multiple variants. The options may be chosen on the product page









Reviews
There are no reviews yet.